Data governance and security
Build trust, not silos.
Integrate governance and security practices throughout your data's lifecycle. From identity verification to data forensics, Y42 safeguards the integrity of your data pipelines.
Identity and Access Management
Secure the lifeblood of your business — your data
Centralize identity verification and implement access controls for both your code and data. Y42's Identity and Access Manager gives you precise control over access rights, down to the most fine-grained permissions.
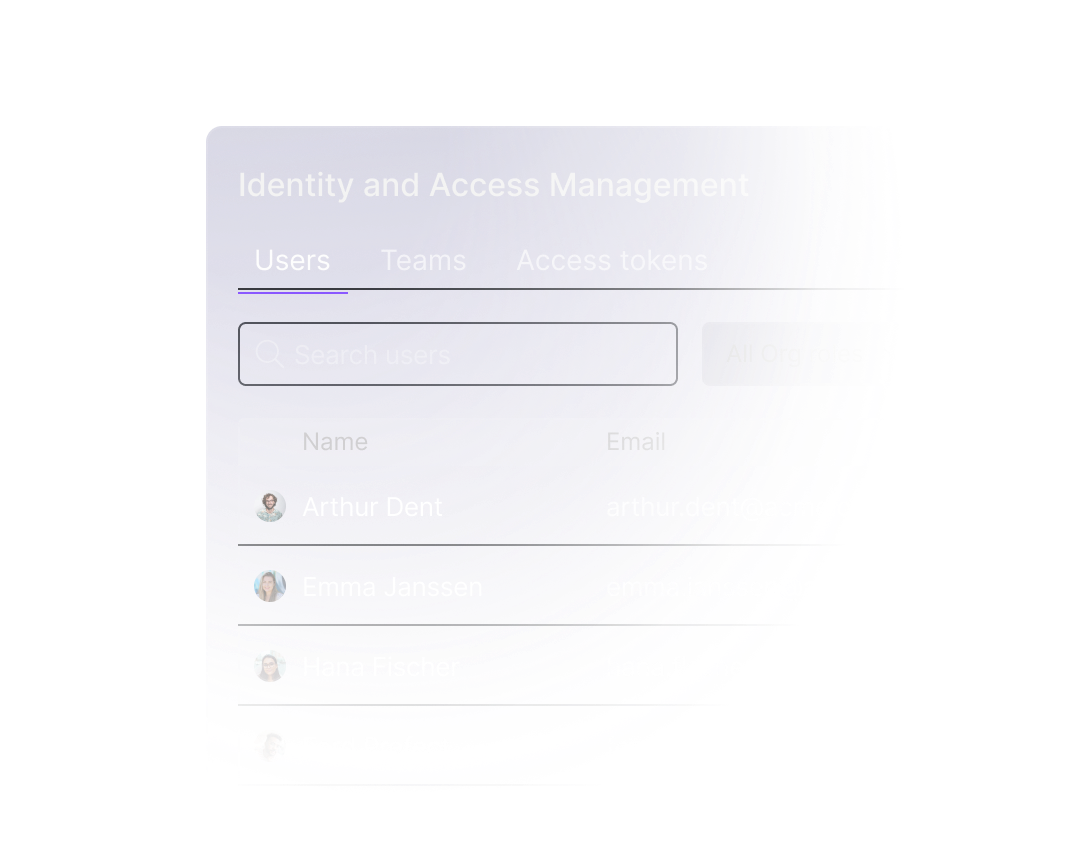
Role-based access control (RBAC)
Assign role-specific permissions in a centralized command center, from generating API keys to defining read/write access for individual spaces.
Explore documentation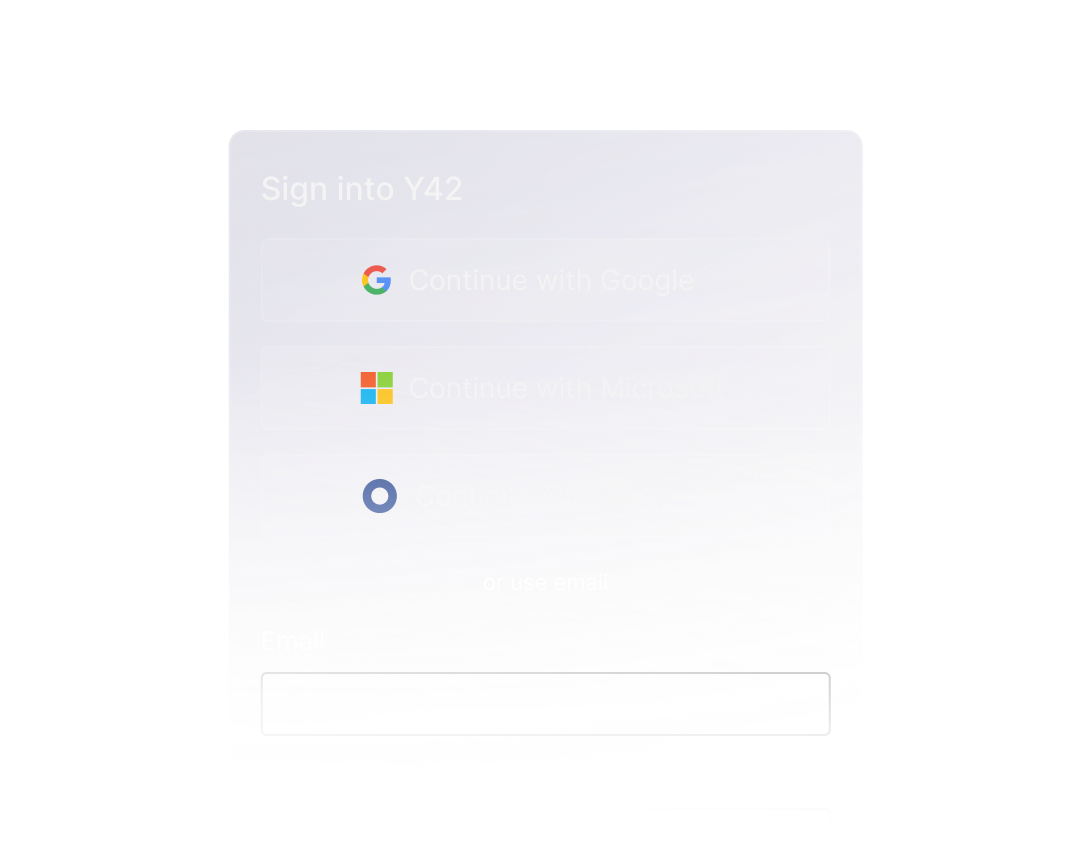
Single Sign-On (SSO)
Sign-in using Google or Microsoft OAuth2, manage authentication via SAML or fully integrate with Okta to combine the ease of SSO with the security of SCIM.
Explore documentation
Two-factor authentication (2FA)
Enhance your Y42 organization’s security by enabling and requiring 2FA — ensuring that each sign-in demands secondary verification to prevent unauthorized access.
Explore documentation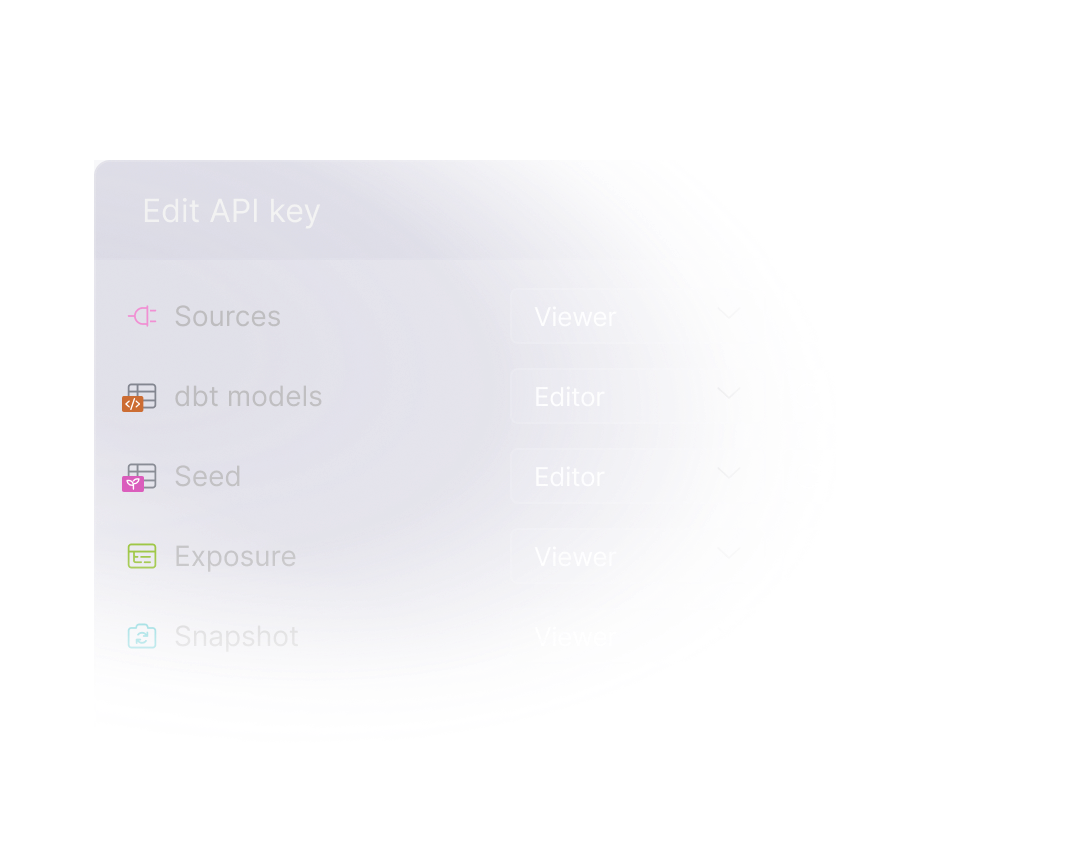
API keys
Generate API keys with set expiration dates, customize their access scope to fit organization or space permissions and manage who can use them.
Explore documentationForensic data analysis
Don't play hide and seek with data discrepancies
Y42's asset change history provides a comprehensive audit log that tracks your data's journey from source to dashboard. Governance isn't just about compliance checklists, it's about the assurance that no detail escapes your scrutiny.
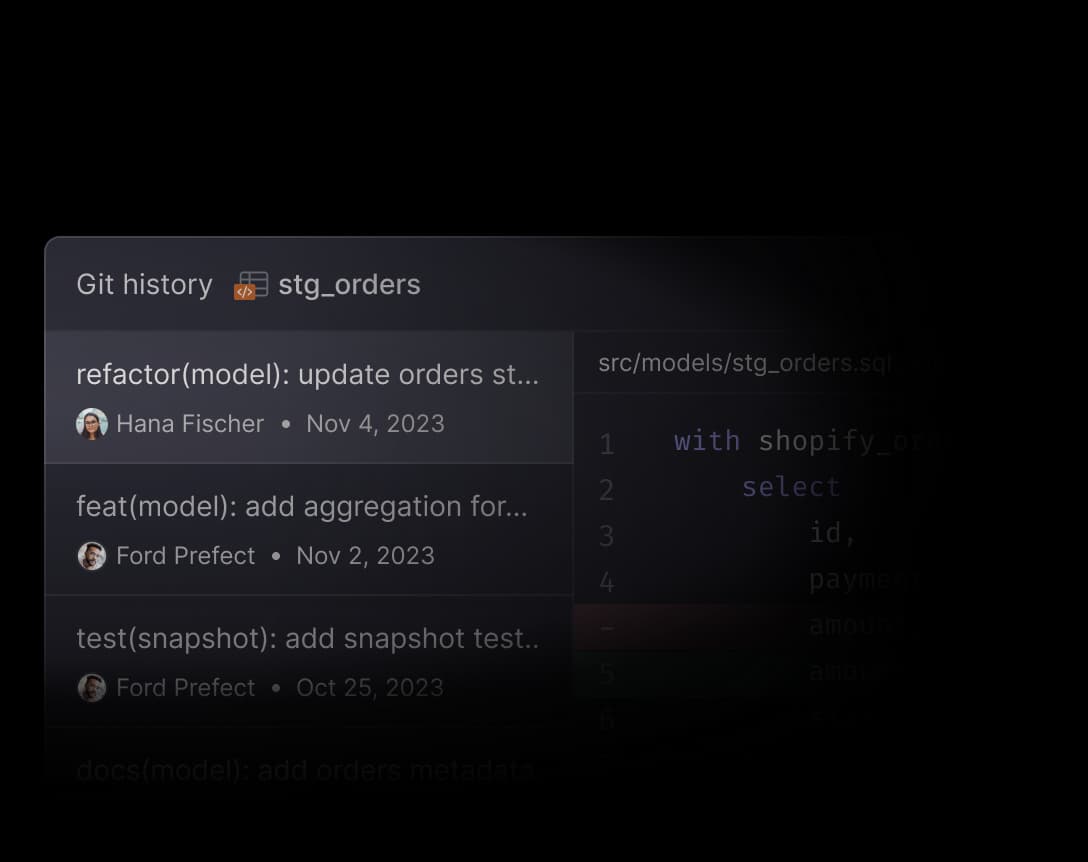
Asset-level change history
Track changes made to any step in your data pipelines with precision. With immutable Git records, you can pinpoint exactly who made a change and when.
Explore documentation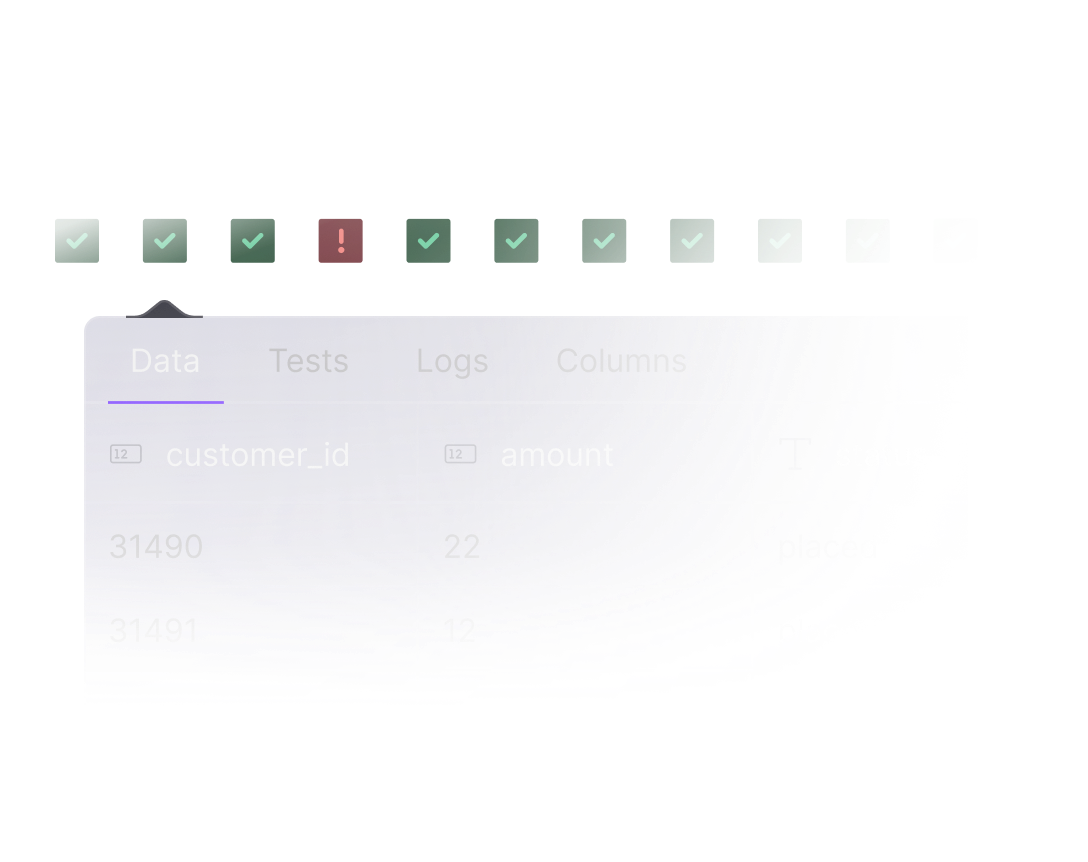
Replay historical data
Retrieve not just historical build details but also previous versions of your data — so you can zero in on the root causes of any data inconsistencies.
Explore documentation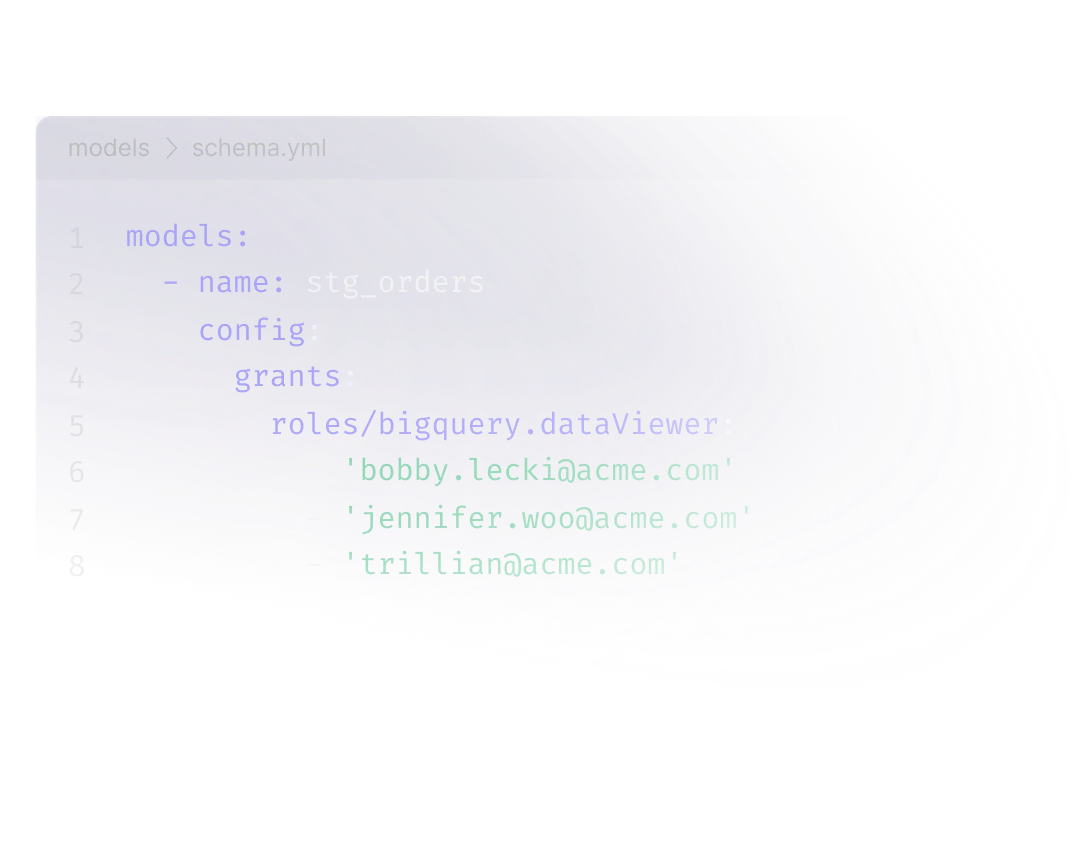
data protection
Automatically apply PII tags and grants
Embed PII tags and grants into any step. Y42 automatically applies these configurations whenever a table is created in your data warehouse, ensuring that your data protection protocols are always in lockstep with the development of your data pipelines.
Explore documentationRegulatory compliance
Security first and always
Y42 rigorously adheres to EU data regulations, offering enterprise-grade security upheld to the highest standards.